How Secure Are Private Key Backup Methods? A Comparative Study
Table of Links
Abstract and 1. Introduction
-
Related Work
2.1 The Alternative-Authenticator Approach
2.2 The Original-Authenticator Approach
-
The Proposed Secret Backup Approaches
3.1 Notations
3.2 Assumptions
3.3 The Direct-Escrow Method
3.4 Our Proposed Algorithms
-
Security and Reliability Analysis
4.1 Security Analysis
4.2 Reliability Analysis
4.3 Recovery Failure Rate Analysis
4.4 Real World Parameters
4.5 Failure Rate Optimization of (k,n)
-
Comparison
-
Conclusion, Acknowledgment, and References
Appendix
5. COMPARISON
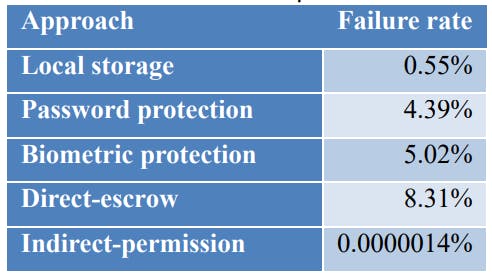
In this section, we compare our proposed indirect-permission method with other private key backup and recovery methods using the recovery failure rate measure in equation (4) based on the same estimated P (insecurity rate) and Q (unreliability rate) measures.
First, we take the paper wallet local storage solution [6] as an example. The paper wallet method prints the private key as a QR code and stores the code offline. For this approach, once the backup is stolen or lost, then the backup is considered a failure since anyone with the QR code can retrieve the private key. If we use the same burglary rate, 0.274%, to represent the worst-case stolen probability as discussed in section 4.4, the computed failure rate is 0.55%, much higher than our approach.
As for the password protection method, an offline backup is encrypted by a password [16]. An adversary must steal the backup and perform a brute force attack to guess the password. Recent research reported that one could guess in 16 days 40% of real-world passwords based on a recently leaked password set using an NVidia GeForce GTX 980 Ti [42]. Therefore, the attack success rate is equal to the stolen rate multiplies the password guessing rate, i.e., 0.4*0.00274=0.0011. On the other hand, the loss rate can also be estimated by the probability that an owner forgets the password. A large-scale survey of password-using habits indicates that 4.28% of users forgot their passwords over three months [64]. Therefore, the recovery failure rate is at least 4.28%, a very high number.
For biometric protection, an offline backup is stored in a biometric-enabled device, such as a fingerprint USB [51]. We take the fingerprint solution as an example for comparison since both the spoofing and the anti-spoofing techniques are relatively mature. In this case, an adversary may steal the backup and spoof through the owner’s fingerprint. Therefore, the attack success rate is equal to the backup stolen rate multiplies the spoof success rate, about 5%, based on an estimate from a fingerprint liveness detection competition [65]. In this case, the loss rate is the anti-spoofing algorithm’s false rejection rate, which is about 5%, as shown in [65]. Therefore, the total recovery failure rate is 5.02%, a very high number too.
For the direct-escrow method, we refer to Vu’s work [52], which encrypts the secret shares using passwords and escrows them to trustees. Since the adversary knows all trustees, a successful attack can be achieved by cheating or colluding enough trustees without causing suspicion and by successfully guessing the passwords. The probability of successful cheating or collusion without suspicion essentially can be computed by equation (2) but with N replaced by n. The loss rate can be calculated by equation (3) with the same F. For fair comparisons, we set the same total number of trustees and the recovery threshold as ours. Then we have an 8.31% failure rate, which is amazingly high due to the easy collusion possibility.
Finally, we list the recovery failure rate of each approach for comparison in Fig. 5 and Table 1 based on (3,5) secret sharing. Note that Facebook also adopts (3,5) secret sharing for its trusted contact framework [22], and hence the (3,5) parameters shall be a good reference for comparison.
In summary, the failure rate of our proposed indirect-permission approach is about six orders of magnitude better than all other results. This fact indicates that our method is both highly secure and reliable.
It is worth noting that the failure rate of both the password and biometric protection are higher than the local storage approach because both approaches emphasize security but not reliability. Therefore, the password and biometric protection approaches are more appropriate for the primary authenticator. On the other hand, the direct-escrow [52] emphasizes reliability more, while its lower security measure severely degrades the failure rate.
Authors:
(1) Wei-Hsin Chang, Deepmentor Inc. ([email protected]);
(2) Ren-Song Tsay, Computer Science Department, National TsingHua University, Hsinchu, Taiwan ([email protected]).