I Built an AI Copilot That Thinks in Exploits, Not Prompts

Hey HackerNoon, it’s Kuwguap again.
A while back, I wrote about building RAWPA, my AI copilot for pentesters, and the tough decision to turn off its initial AI feature because it wasn’t delivering. That was a lesson in knowing when to pivot. Today, I want to share the next chapter in that journey: how RAWPA evolved from a collection of useful tools into a system with a thinking brain.
The story isn’t a straight line. It’s a tale of community feedback, manual data parsing, and a sleep-deprived “aha!” moment that changed everything.
After the initial pivot, my focus shifted to making RAWPA undeniably useful, fast. I opened it up to a small group of early testers (we’re at 22 now, with about half using it daily!) and the feedback was immediate and invaluable.
One of the best ideas came from a connection in the community: “Why not integrate LOLBAS, GTFOBins, and WADCOMS directly into the app?”
It was a brilliant suggestion. The integration process itself was a perfect example of the unglamorous side of development. Getting LOLBAS onboard was a breeze; they have a fantastic API designed for exactly this kind of thing.
The other two were a different story. It was a manual hustle. I had to pull the project files directly from their GitHub repos and write a parser for my database. Thankfully, they were structured in markdown, which made grepping for the data I needed manageable. It was a grind, but it made the app instantly more powerful. Along the way, I added smaller toolkits like a Reverse Shell Generator and an OSINT toolkit.
The app was growing. It was becoming a solid, hierarchical assistant. But I knew it was still missing a soul. It was a sculpture, waiting for a brain.
Part 2: The “Bag of Bricks” Moment and the AI Brain(kinda)
I’d been running on fumes, coding non-stop. One night, I finally got about six hours of sleep. I woke up to an idea that hit me like a bag of bricks: the Neural Pathway Methodology.
I saw with perfect clarity how RAWPA could transcend being a static playbook. It could learn.
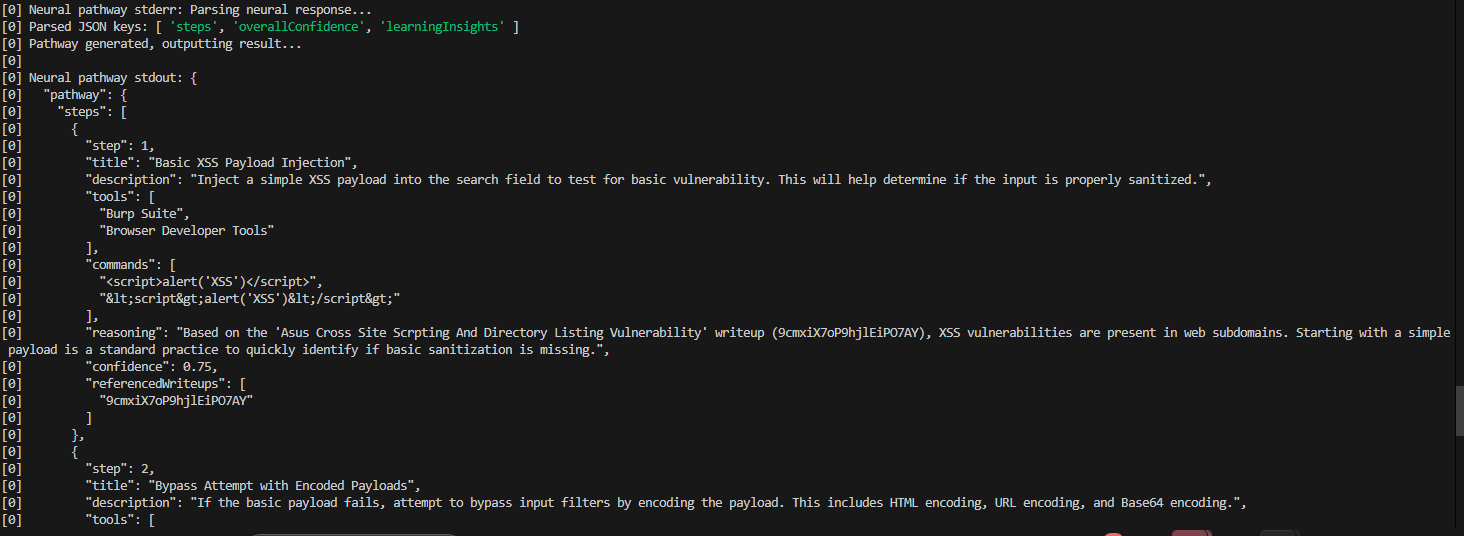
This isn’t some generic LLM wrapper. I’d already wrestled with implementing a RAG (Retrieval-Augmented Generation) model and knew the hassle involved. This new idea was different. The Neural Pathway Methodology gives RAWPA a specialized brain—a neural network—trained specifically on a massive dataset of real-world pentest writeups, methodologies, tools, and techniques.
It’s the difference between a tool that can look things up and a system that can learn from the collective experience of the entire cybersecurity community.
How the Neural Brain Works
The concept is to fuse the structured knowledge of the community with the reasoning power of a modern LLM. Here’s the high-level flow:
- You Provide the Context: You tell RAWPA where you are in your pentest, what you’ve found, and any other relevant details about the target.
- The Neural Net Analyzes: The neural network, which has been trained on thousands of pentest reports, analyzes your input and synthesizes the most relevant patterns and techniques from its knowledge base.
- Gemini Collaborates to Generate a Pathway: The synthesized knowledge is then passed to Google’s Gemini LLM with a custom, context-aware prompt. Gemini reasons over the information to generate a unique, step-by-step pathway for you. This includes actionable steps, specific tool commands, and most importantly, the AI’s reasoning for why it’s suggesting that particular action.
- It Learns from Feedback: It’s a living system. Users can rate the pathways, and that feedback is used to continuously refine the neural network. The more it’s used, the smarter it gets for everyone.
Why This is a Leap Forward
This approach isn’t just about adding an “AI” label. It’s about creating:
- Adaptive Intelligence: RAWPA is no longer a static checklist. It learns from new, real-world writeups, allowing it to adapt to emerging threats and techniques.
- Truly Personalized Guidance: The pathways aren’t generic. They are tailored to your specific context, making the advice far more actionable and relevant.
- A Bridge Between Human and AI Expertise: It combines the wisdom of countless human-written reports with the creative problem-solving of an LLM.
The journey of building RAWPA has been a rollercoaster, but for the first time, it feels like it has a soul. It’s evolving from a simple assistant into a dynamic partner that helps rejuvenate a pentester’s train of thought.
This is a community-driven effort. If you have methodologies, ideas, or suggestions, I would love to hear them. The best way to reach out is on LinkedIn At the end of the day, I believe RAWPA will help someone get unstuck and learn something new. And for me, that’s good enough and my blog.
The project is community-driven at its core, and I’m always looking for testers and contributors. Check it out at https://rawpa.vercel.app/ and let me know what you think. The brain is just getting started.